Your message has been sent!
Thank you
- cybersecurity
- crypto
- August 22, 2023
The Web3 Security Engineer's Arsenal: Must-Have Tools for Auditing Smart Contracts
Web3 security reviews require a specialized toolkit to thoroughly analyze smart contracts, simulate attacks, and certify code is free of vulnerabilities. This article by Hexens' own rootNad explores essential frameworks, static analyzers, debuggers, and mindsets security engineers need to conduct robust audits.
But let's start from the beginning — the first and perhaps most essential tool for conducting security audits is an Integrated Development Environment (IDE) and a text editor.
Code Editors
Currently, the most popular and widely used code editor is Visual Studio Code (VSCode). Several factors contribute to its popularity. Firstly, VSCode offers a wide range of extensions that can turn it into an IDE for virtually any programming language. This versatility is particularly valuable in the realm of security audits, where the diversity of technologies is significant. Additionally, VSCode provides flexible customization options for appearance and color schemes, promoting comfortable visual perception and reducing eye strain.
The most important language in the Web3 field is Solidity. For this language, there are numerous useful plugins. Here are some of the most valuable and interesting ones:
- Solidity Plugin by Juan Blanco: This versatile plugin is independent of the chosen framework.
- Solidity Plugin by Nomic Foundation: This plugin also supports various frameworks but shines most when used with projects utilizing the Hardhat framework.
- Solidity Visual Developer Plugin: This plugin offers a plethora of features, and one of the most demanded is the ability to generate dependency graphs between contracts and functions.
However, despite all the advantages of VSCode, it is not without its drawbacks. One of the most significant issues for me is the ability to work with Git and view changes (git diff). In such cases, I prefer using the IntelliJ IDE with a Solidity language plugin. This IDE implements, arguably, the most convenient code comparison feature I have used. Moreover, with IntelliJ IDE, you can audit not only smart contracts but also analyze the blockchain as a whole, along with the entire blockchain infrastructure.
Of course, the same tasks can be accomplished using VSCode, but the JetBrains IDE provides more convenient tools for working with specific languages. For instance, there's GoLand for the GO language, CLion with the Rust plugin boasting the market's best debugger for Rust, and PyCharm for auditing oracles and libraries for blockchain work.
It would also be relevant to mention a new product for auditors — AuditWizard. Within this tool, you'll find a built-in system for creating and generating pre-formatted reports. One of the features of AuditWizard is its integration with ChatGPT, which significantly enhances the report-writing process. With ChatGPT's assistance, AuditWizard can provide concise summaries of contract functionalities and operations, enhancing the clarity and depth of your audit reports. The platform also incorporates the prowess of static code analyzers like Slither. Presently, AuditWizard offers a user-friendly interface accessible directly through your browser. You can get started with just a browser and a link to the project's GitHub repository. Moreover, from the main page, you can conveniently access projects participating in bug bounties or audit contests. At the moment, AuditWizard is in beta version, you can try it here.
Additionally, it's important to mention Remix IDE, which holds a significant place in the web3 development sphere. In the web3 community, Remix is often seen as an ideal environment for newcomers as it requires no additional installations or configurations to get started. This is convenient for those just beginning their journey with blockchain technologies and smart contracts. Remix can also be valuable for auditors. It allows for quickly executing small code fragments to test hypotheses and evaluate gas costs. Furthermore, Remix provides debugging tools that can be very useful for auditors and developers. We will also discuss debugging in the debugger section. Hence, Remix IDE plays a significant role in the web3 development ecosystem, offering ease of use for beginners and providing valuable tools for auditors and developers.
Frameworks
The next important tools for auditing are smart contract development frameworks such as Hardhat and Forge. Let's take a closer look at each of them:
- Hardhat is a development, testing, and deployment environment for smart contracts with a flexible plugin system. For writing tests, scripts, and project configurations, you can use JavaScript/TypeScript depending on your preferences. All project dependencies are managed using JavaScript package managers — npm or yarn. Hardhat also provides a local blockchain that can be easily configured for testing smart contracts. Additionally, Hardhat offers convenient interfaces for testing contracts in both test networks and forking the original network. Developers have also implemented logging features for smart contracts, making the debugging process more straightforward.
- Forge (formerly Foundry) is also a development, testing, and deployment environment for smart contracts, but with some differences. Forge uses the Solidity language for writing tests and scripts. This solution has simplified the entry into the web developer and web3 security specialist professions, as now only knowledge of the Solidity language is required to get started. Forge also provides a local blockchain for conducting tests. Moreover, the Forge development team has incorporated "fuzzing" testing capabilities into their framework, which greatly eased the lives of many professionals in the web3 field. The framework is also capable of providing test execution tracing, simplifying the development process. Just like in Hardhat, logging tools are present in Forge.
- Truffle is one of the oldest frameworks for smart contract development, developed by ConsenSys in 2016. Over time, Truffle evolved into a complete suite of tools, including Truffle itself, Ganache, Drizzle, and a VSCode extension. Truffle itself is a comprehensive solution that combines development and testing environments. A few words about the components of Truffle:
- Ganache is a local blockchain environment designed for testing and development in a secure isolated setting. It has two modes of usage: GUI and CLI.
- Drizzle is a set of libraries within the Truffle Suite that simplify data synchronization for dApps during development.
Which framework to choose? This question can be answered fairly simply. If you're unfamiliar with JavaScript/TypeScript languages and don't have time for learning, then go with Forge. Otherwise, from an auditor's perspective, you can consider the framework on which the project is written. If a specific framework's support is not present in your project, the choice is up to you.
Static Code Analyzers
In this article, we'll discuss static analyzers specifically designed for the Solidity language.
- First, let's talk about arguably the most popular static code analyzer developed by TrailOfBits called Slither. Slither is an open-source static analyzer. It doesn't analyze the Solidity code itself, but its abstract syntax tree is obtained through compilation by the solc compiler. Here are a few types of vulnerabilities that Slither can detect: Incorrect ABI encoder usage, State variable shadowing, Unprotected upgradable contract, and unprotected call to self-destruct. The full list can be found on GitHub.
- Additionally, for Slither, there are additional detectors that have been developed by the pessimistic.io team and named Slitherin. These supplementary detectors expand Slither’s functionality, enabling the identification of additional types of vulnerabilities and potential issues. The pessimistic.io team has introduced the following detectors into Slitherin — Unprotected Setter, Token Fallback, Read-only reentrancy, and others. The complete list of additional detectors added by the Pessimistic team can be found on GitHub.
- There's also a static code analyzer developed by the ConsenSys team called Mythril. This analyzer uses symbolic execution to analyze the source code. Mythril executes the Solidity code with various input data and analyzes its execution. Here are a few vulnerabilities that Mythril can detect: Delegatecall to Untrusted Contracts, Unprotected Ether Withdraw, Reentrancy, Integer Overflow, and Underflow. You can find a complete list here.
- Echidna was developed by TrailOfBits for fuzzing/property-based testing using the Haskell language. Echidna conducts analysis tailored to each project. It creates invariants or solidity function-based test cases from the source code and input/output patterns. These invariants are then executed using random transactions, and their results are examined.
When working with static code analyzers, keep in mind that vulnerabilities in smart contracts can be related to unexpected interactions between different parts of the contract or between different contracts in the system. This can pose challenges for static analyzers, as they might lack sufficient information about the execution context. Nevertheless, these tools still have a role in the process of securing smart contracts. They are capable of detecting certain basic vulnerabilities and syntactical errors. Furthermore, a static code analyzer can be part of a comprehensive security approach, combined with other tools and methods such as dynamic testing and code auditing. Thus, while static analyzers cannot guarantee complete security for smart contracts, they remain a valuable tool in the arsenal of auditors and developers for detecting basic vulnerabilities and enhancing overall code security.
Debuggers
Certainly, transaction debuggers play a vital role in ensuring the security and efficiency of smart contracts. They allow developers and auditors to monitor the state of contracts during transaction execution, enabling the detection and resolution of issues and vulnerabilities.
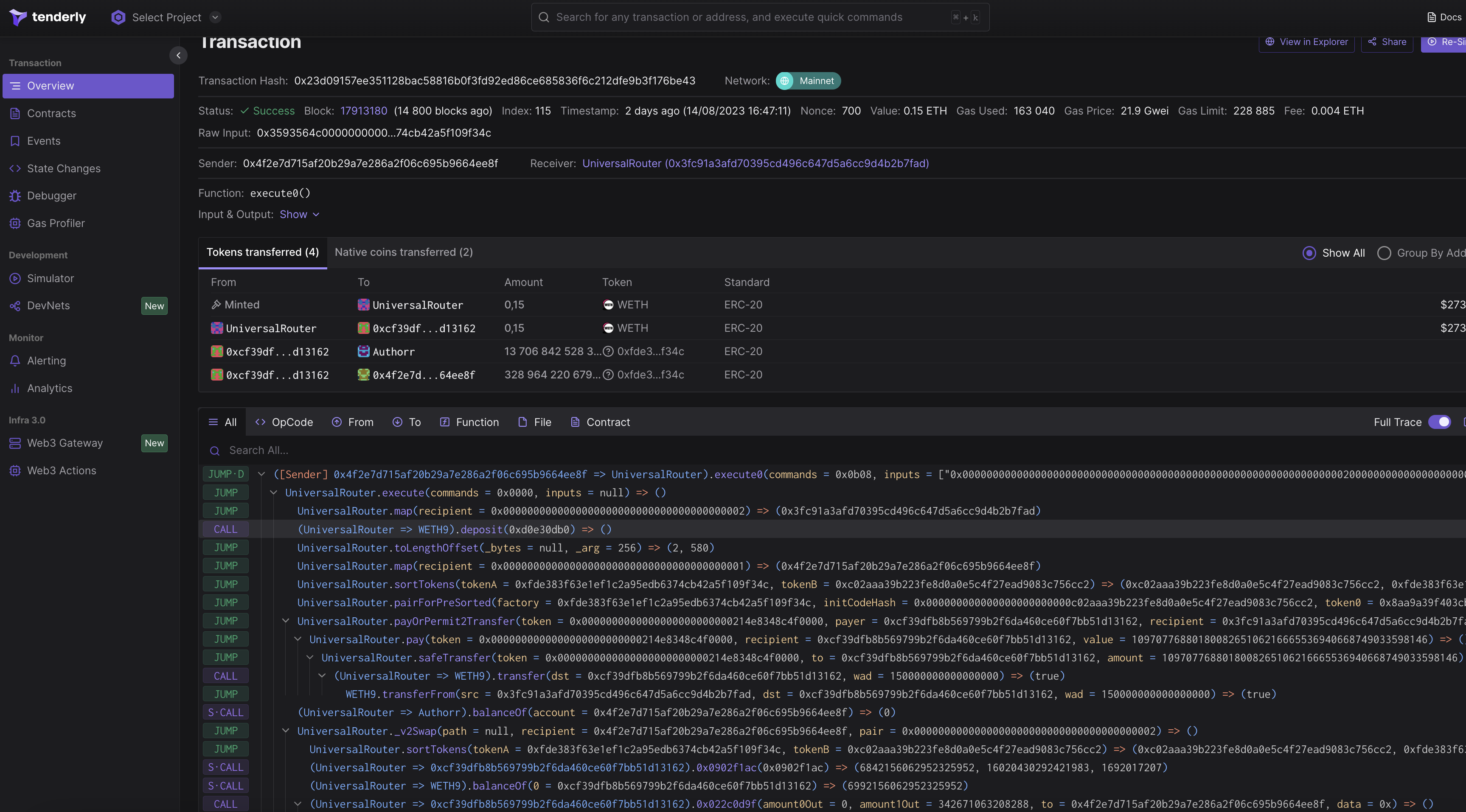
- First, let's delve into the first debugger — the one from Tenderly. Tenderly is a powerful debugging, smart contract simulation, and extensive feature tool. Tenderly Debugger enables real-time monitoring of smart contract execution and in-depth analysis of their behavior. One key feature of Tenderly is the ability to fork the blockchain. You can create local blockchain copies based on current data, allowing debugging and analysis in realistic conditions without the risk of fund loss. Tenderly also provides transaction monitoring. You can track transaction and contract execution, receiving detailed information about each operation. It's important to note that for using the Tenderly Debugger, your smart contract needs to be verified and present in the Tenderly block explorer. This might limit its use for certain audits, but it remains a valuable tool for developers and auditors, offering powerful functionalities for smart contract analysis and debugging.
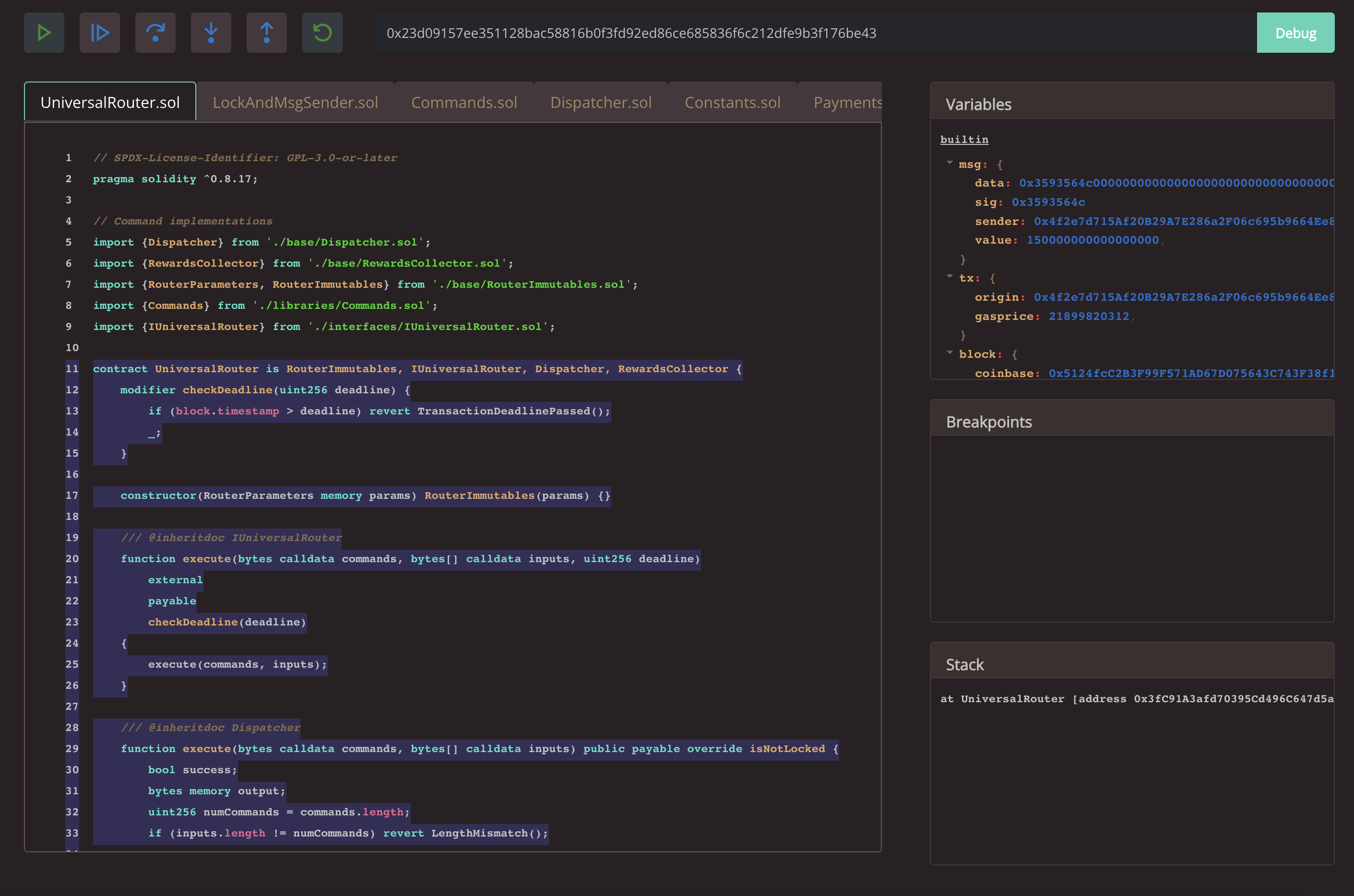
- Now let's take a closer look at the debugger within the Foundry framework (formerly Forge). Foundry has incorporated a debugger into its framework for smart contract development and testing, which truly eases the work of many auditors and developers. The Foundry Debugger provides a console interface for debugging functions. This allows for a detailed analysis of function behavior and control over their execution. Additionally, there's the capability to pass specific calldata (data sent in a transaction) during function execution. This enables the simulation of various scenarios and analysis of function behavior with different input data. Another remarkable feature of Forge's debugger is its integration with fuzzing testing. If the function you're debugging is being tested with fuzzing (automatic testing with diverse input data), Foundry's debugger will open on the first failed test or the last successful test. This allows for quick analysis of situations that might cause issues in the function. Overall, the Foundry debugger within the Forge framework provides powerful tools for smart contract analysis and debugging, simplifying the development and audit process.
- Finally we should consider the debugger from Truffle. Until recently, Truffle only had a CLI debugger. The Truffle CLI debugger offers the ability to debug transactions from different blockchain networks. With it, you can set breakpoints, analyze contract instructions, and view its current state. Truffle recently released a GUI version of their debugger integrated into the Truffle Dashboard. This debugger provides all the functionality of the CLI debugger in a more user-friendly format. To use the GUI debugger, you'll need a wallet that you can connect to the web version of the debugger, along with the transaction hash you want to analyze. However, it's worth noting that this debugger has a few drawbacks. The main drawback of this debugger is its relatively low execution speed.
Tools for ZK systems
Now we will move on to discussing Zero-Knowledge (ZK) systems audits. Audits of ZK systems cover a multitude of components; however, in this article, we will only explore a few of them.
- Let’s start with arithmetic circuits. Arithmetic circuits play an important role in the field of cryptography and security. They are used to create systems based on constraints that provide completeness and soundness. Currently, one of the most popular languages for writing arithmetic circuits is Circom. Circom was developed by the iden3 team. For Circom, there is also a static analyzer called Circomspect, developed by TrailOfBits. This analyzer is designed to detect various security issues in arithmetic circuits created using Circom. Among the detected issues are shadowing variables, side-effect-free assignments, signal assignments, and more. The complete list of detectable problems can be found on GitHub.
- Next, let’s focus on the Polynomial Identity Language (PIL) — a language utilized in the development of the Polygon zkEVM’s state machines. For PIL, there exists a static analyzer developed by Hexens called Piller. This tool is open source. Piller allows creating custom verification modules and using APIs that provide all the information available through the compiler, including:
- Parsed expression and polynomial maps that contain reference data between each of them
- Get polynomials by their type (committed, constant, intermediate)
- Filtering the polynomials with regex
- Get the specific type of expressions (e.g. EXPR = 0, EXPR = 1, etc.)
- Find expressions based on a template PIL emulation
Vulnerability Tracking Systems
I'd also like to discuss another important tool for auditors that are used for reporting vulnerabilities. Both solo auditors and auditing teams need an efficient way to document, track, and discuss identified vulnerabilities.
- Let's start by looking at Jira, the tool from Atlassian. Jira is a project management system organized in the form of boards. It also supports integration with corporate chat platforms like Slack. Jira offers an attractive design and flexible customization to meet various needs. However, it's important to note that Jira is a commercial product that requires a paid subscription.
- A good alternative to Jira could be the Trello platform. Trello also provides project management tools in the form of boards. It has a simple interface and integration with other popular tools. Trello also allows fine-tuning of boards and cards. There's a free version of Trello that allows you to create up to 10 boards and a paid version with unlimited boards and additional features.
- Another option could be using Notion. It serves not only as a project management system but also as a platform for creating notes, text documents, to-do lists, and more. Notion supports creating boards and customizing them according to your preferences. It also includes an AI-powered assistant. Use of AI requires any of the paid subscription options and the AI subscription itself.
The choice of a vulnerability reporting tool depends on your needs, preferences, and available resources. Each of these tools offers convenient ways to organize, track, and discuss vulnerability information in projects.
What else do you need?
Certainly, let's also discuss a few tools that don't fall into specific categories but can be useful for auditing smart contracts.
- Let's take a look at the resource evmcodes. This resource is a valuable collection of all the opcodes used in the EVM (Ethereum Virtual Machine). Each opcode comes with a detailed description of its functionality and is accompanied by small examples of its usage. An interesting feature of this resource is the ability to test some opcodes directly on the website. "EVM Codes" also provides a playground where you can execute any EVM assembly sequence, view the execution result, and learn the gas cost of that sequence. This provides a convenient environment for experimentation and understanding of how different opcodes and their sequences work. The evmcodes resource is a valuable tool for smart contract developers and auditors, helping them gain a deeper understanding of the inner workings of the EVM and effectively utilize opcodes in smart contract development and testing.
- Also, it's important not to forget that one of the key tools for any auditor is the broader community. The community often shares crucial aspects such as attack vectors, articles, research, warnings, and more. What the community provides above all is collective knowledge and experience. It's particularly valuable to follow the community during major incidents or breaches. These are often discussed in communities, and you can learn how the incident occurred, what caused it, which attack vectors were used, and so on. As platforms to stay connected with the community, I would recommend looking into Twitter and Telegram chat groups like the “ETHSecurity Community”. They offer up-to-date information, discussions, and the opportunity to exchange knowledge with fellow community members.
- Lastly, the final tool we'll discuss might come as a surprise — it's the mindset of a security engineer. At first glance, this concept might not seem directly related to an auditor's tools. However, in reality, mindset plays a crucial role in the work of a security auditor. After all, none of the mentioned tools will make you a top-tier expert, but your mindset will. The mindset of a security engineer is a kind of primary "weapon." It shapes your understanding, approach, and priorities during security audits. It encompasses awareness of potential vulnerabilities, in-depth code investigation, a habit of seeking weaknesses, and thorough checks for potential threats in contracts. It's your ability to think like a malicious actor, to preempt vulnerabilities before someone else discovers them. Your mindset enables you to effectively apply all tools, uncover complex vulnerabilities, and put yourself in the attacker's shoes. Ultimately, the mindset of a security engineer is a key factor in ensuring robust protection for smart contracts and blockchain platforms as a whole.
